The typical K-12 school system has the same basic security needs as any modern university campus: centralized management and control of security systems and procedures, and a strategy for staying ahead of threats while protecting earlier investments. In both cases, the latest open-architecture Physical Access Control System (PACS) solutions offer an infrastructure that is flexible, scalable, and can easily be upgraded to strengthen security and add capabilities without changing the hardware.
Building a Future-Safe Foundation
A future-safe PACS infrastructure operates with any access control software and add-on solutions ranging from parking gates to additional IT security. This requires a highly flexible and non-proprietary open-architecture framework with modern security protocols, technology interoperability, and open Application Programming Interfaces (APIs) that enable hardware to be integrated into any access control system software or security application.
An infrastructure like this ensures scalable, flexible, and unified PACS and security management with a more streamlined operations workflow. Rather than having to monitor different access control, video surveillance, intrusion alarm, and other programs, security personnel have centralized command and control. They can streamline daily operations and reporting and easily add or remove cardholders, adjust access areas, and create access schedules and audit logs for incident investigations. Unreturned cards can be turned off. Lockdown and emergency egress areas can be defined and activated instantly. It is also easier and less time-consuming to train new security personnel in this unified environment that, from a cybersecurity perspective, also makes firmware updates less intrusive.
The path to this infrastructure often starts with a single modernization need, i.e., adding 4K security cameras or replacing physical badges with mobile credentials used with smartphones. Wherever journey starts, the course it takes at the K12 level is remarkably similar to that of the most technologically advanced university.
First Things First
Before campus administrators can consider advanced security and other capabilities, they first must harden their existing infrastructure. This requires a vulnerability assessment and the ability to prioritize needs and plan a smooth migration to a more secure and adaptable PACS.
There was a time when campus security started and ended with doors, locks, and keys. But even after they replaced keys with a PACS and ID cards, not every campus kept ahead of security threats. Many still use low-frequency 125 kHz-based contactless card technology invented decades ago. These proximity – also known as Prox – cards simply transfer unencrypted RFID signals to a reader. All it takes is a $30 cloning device or trip to a grocery store’s key-making kiosk for people to make as many copies of a stolen card as they want. The technology should have been replaced long ago when more secure high-frequency card technologies were introduced.
While the security hardening process may be more complex at a university with many different systems than in a closed K12 environment, each campus benefits from this future-safe PACS foundation. Budget often arrives in phases, and this infrastructure supports incremental additions that can be executed across an extended timeline without requiring hardware changes.
Three Basic Building Blocks
The three PACS building blocks are credentials (cards and mobile), readers, and panels. Each must be future-safe so administrators can address evolving threats and add capabilities when needed.
Credential offerings should support multiple form factors and communication protocols. All high-frequency credential choices should be based on peer-reviewed global standards and offer essential security features like secure messaging and provide a smooth migration path from vulnerable legacy technology to modern and secure options. The most secure options implement AES128 encryption, a secure channel for protecting card data from man-in-the-middle attacks, and a random unique identifier (UID) for protecting user privacy. Some options go further to protect a credential’s identity data through key diversification, authentication signatures and encryption, and enables mobile and wearable form factors.
Readers need to support the widest possible range of credential technologies, plus Near Field Communications (NFC) and Bluetooth Low Energy (BLE) to enable the use of mobile credentials. It is important to evaluate a reader’s range, mobile performance, and administration capabilities, and ensure it supports the Open Supervised Device Protocol (OSDP) so technicians with iOS and Android devices can reconfigure and update them in the field. OSDP also enables technologies to be added and turned on and off without visiting each reader.
All readers are connected to PACS panels that make all decisions about whether to unlock a door for someone presenting their credential. They communicate with access control software to monitor events, allow cardholders to be added and removed, make changes to access rights, and store and provide event audit trails, among other tasks. These panels should be based on an open platform and support OSDP for remote reader management.
Together, these future-safe PACS building blocks enable security administrators to choose whatever access control software works best for current and future needs. They can upgrade their PACS as required, including moving to a trusted ecosystem of cloud-connected access control devices, applications and mobile identities.
Adding Security and Functionality
During the pandemic, campuses with a future-safe PACS infrastructure demonstrated how important it is to quickly add capabilities that improve resilience and adaptability. Two examples are Bay State College, which implemented location-based physical-distancing and contact-tracing solutions to identify and mitigate COVID-19 outbreaks, and Vanderbilt University, where mobile IDs for “touchless” access control eliminated badge and ID card issuance touchpoints and contact with cards, readers or keypads.
More recently, Vanderbilt leveraged HID Mobile Access® to deploy campus IDs on iPhone and Apple Watch through Apple Wallet. Firmware on the university’s PACS readers was upgraded using HID Reader Manager to extend support for NFC-based credentials in Apple Wallet. The university uses the HID Origo™ Mobile Identities API integrated with CS Gold®, a higher education transaction system from CBORD, for credential lifecycle management.
These and other advanced capabilities such as location-based emergency mustering are not just for higher education. K-12 students became much more digitally savvy during a year of remote learning and may now be ready to embrace college ID experiences that have gone beyond security and convenience to become a digital lifestyle. Enabling high schoolers to use these IDs to check out books or pay for meals has the potential to not only improve security but also better prepare them for a safer college experience. Even with the university security infrastructure to protect them, co-eds are only safe if they want to be. Teaching them to embrace security protocols in high school, in an environment whose PACS infrastructure is much like what they will experience in college, will pay off in the future.
In the meantime, basic K-12 security hardening can also include adding elements like intrusion detection, video intercoms, and authenticating visitors outside the vestibule. Many districts are integrating metal detectors, gunshot detection and license plate recognition at the parking entrance (see Fig. 1). Location-based technology such as that used for university contact tracing is also being evaluated by schools that, for instance, seek to comply Florida’s panic-button mandate – it only works if law enforcement and first responders know where people are when they push the button.
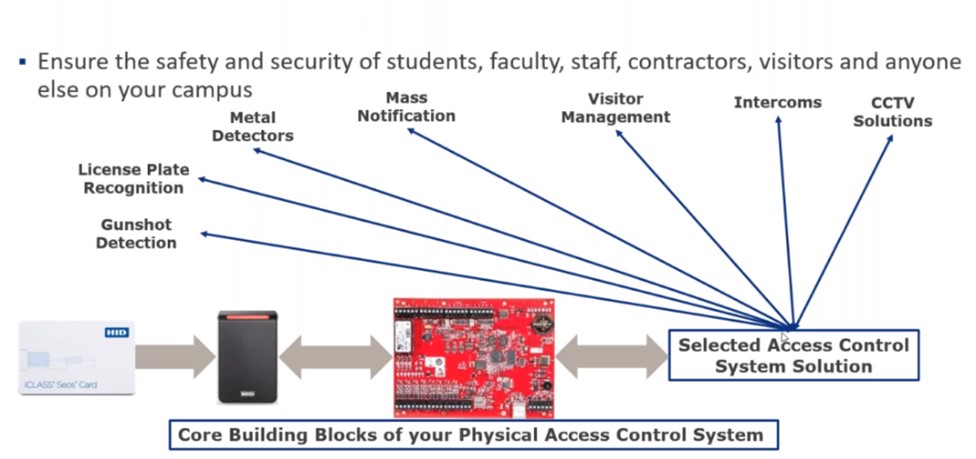
Figure 1: The building blocks and expansion capabilities of a successful K-12 PACS.
Ensuring a smooth migration to a future-safe PACS generally requires working with a security integrator that understands how to leverage readers that are backward-compatible with older card technologies. This ensures old hardware can be replaced over time prior to a campus-wide cut-over to the latest secure high-frequency cards at the beginning of a new school year.
In addition to PACS readers, security administrators may also need to integrate other types of readers into their future-safe platform, such as those used in Point of Sale (POS) applications, at the library or vending machine, and in the recreation center. They also will likely continue to need secure issuance functionality, even if they also adopt mobile IDs. Cloud-based issuance platforms enable remote management of all card design, encoding to printing. An administrator in a card office or any remote location can seamlessly create and encode new cards, issue replacements, and manage print queues through one trusted system using a tablet, laptop, or any device with a web interface. Users can pick up their cards at many different locations rather than the main card office.
A Journey – Not a Destination
Optimizing security is a journey toward a destination that can never be reached in today’s ever-changing threat environment. With a future-safe PACS infrastructure, administrators can stay ahead of these threats without worrying about a rip-and-replace hardware upgrade. All improvements can be implemented incrementally when budget permits. K12 administrators can focus on replacing decades-old security technologies with a future-safe PACS foundation to which they can add capabilities over time. University administrators can unify what is so often a hodge-podge of security systems so that, as they continue to strengthen security while improving the campus experience, they have centralized management and an end-to-end chain of trust.
- 4 ways to encourage play in education - April 25, 2024
- It’s time to pay student teachers - April 25, 2024
- The evolving requirements of a K-12 school network - April 24, 2024

